Data Communication and Computer Network
By Paribesh Sapkota
Introduction:
Data communication and computer networks play a pivotal role in enabling the exchange of information and resources between computers. This field encompasses various aspects, including data transmission, networking, communication protocols, and the hardware involved.
Importance of Networking:
Communication is medium that helps us to drive our day to day professional and personal operations. Where computer networking acts as base of everything as the best and most important IT solutions. Below is list of points that we do with the help of computer networks, or things that we get benefited with the help of computer networks or it has become possible or effective due to computer network. Let us know all points and after that, we can understand importance of computer networking.
- Provides best way of business communication.
- Streamline communication.
- Cost-effective resource sharing.
- Improving storage efficiency and volume.
- Cut costs on software.
- Cut costs on hardware.
- Utilizes Centralized Database.
- Increase in efficiency.
- Optimize convenience and flexibility.
- Allows File sharing.
- sharing of peripherals and internet access.
- Network gaming.
- Voice over IP
- Media Center Server.
- Centralize network administration, meaning less IT support.
- Flexibility.
- Allowing information sharing.
- Supporting distributed processing.
- User communication.
- Overcoming geographic separation.
Computer networking has also played a crucial role in the development of new technologies like cloud computing, big data analytics, and the Internet of Things have all benefited greatly from computer networking (IoT). Businesses are now able to gather and analyse enormous volumes of data, automate their procedures, and make better choices faster thanks to these technology.
In general, we can see “Communication” and “Sharing”, that is all networking is about in simple terms. It enables everything that we do today. In the current scenario, the business would not work without computer networking and our personal and social life will also feel like it has been stopped.
Data Communication Media:
Data communication involves the transmission of data from one device to another, and various types of media are employed for this purpose. These media can be categorized into two main types: guided media and unguided media.
1. Guided Media: Guided media, also known as bounded or wired media, involves the use of physical cables or wires to transmit signals. Here are some common types:
- Twisted Pair Cable:
- Consists of pairs of insulated copper wires twisted together.
- Used for telephone lines and local area network (LAN) connections.
- Types include unshielded twisted pair (UTP) and shielded twisted pair (STP).
- Coaxial Cable:
- Contains a central conductor surrounded by an insulating layer, a metallic shield, and an outer insulating layer.
- Used for cable television (CATV) and broadband internet connections.
- Fiber Optic Cable:
- Utilizes thin strands of glass or plastic to transmit data as pulses of light.
- Offers high bandwidth, immunity to electromagnetic interference, and long-distance transmission.
- Common in high-speed internet connections and long-distance communication.
- Optical Fiber:
- Similar to fiber optic cables but without the protective sheath.
- Used in short-distance applications like connecting devices within data centers.
- Twisted Pair and Coaxial Hybrid Cable:
- Combines characteristics of both twisted pair and coaxial cables.
- Used for high-speed data transmission in certain networking applications.
2. Unguided Media: Unguided media, also known as unbounded or wireless media, involves the transmission of signals without the use of physical cables. Here are some common types:
- Radio Waves:
- Used for wireless communication, including radio and television broadcasting.
- Common in mobile communication systems.
- Microwaves:
- Use high-frequency electromagnetic waves for communication.
- Employed in point-to-point communication, such as long-distance telephone and television transmission.
- Infrared Waves:
- Use infrared light for short-range communication.
- Common in devices like remote controls and wireless data transfer.
- Satellite Communication:
- Involves communication via signals transmitted to and received from satellites.
- Used for long-distance communication, including television broadcasting and global positioning systems (GPS).
- Bluetooth:
- Short-range wireless technology used for connecting devices such as smartphones, laptops, and peripherals.
- Wi-Fi:
- Wireless technology that allows devices to connect to a local area network (LAN) without physical cables.
- Widely used for internet access in homes, offices, and public spaces.
Data Transmission across Media:
Data transmission involves the movement of data from one location to another, and it can occur through various types of communication media. The choice of transmission media depends on factors such as data rate, distance, cost, and the specific requirements of the communication system. Here are some key aspects of data transmission across different types of media:
1. Twisted Pair Cable:
- Characteristics:
- Consists of pairs of insulated copper wires twisted together.
- Commonly used for telephone lines and local area network (LAN) connections.
- Susceptible to electromagnetic interference.
- Data Transmission:
- Typically used for short to medium distances.
- Supports data rates suitable for voice and moderate-speed data communication.
2. Coaxial Cable:
- Characteristics:
- Contains a central conductor, insulating layer, metallic shield, and outer insulating layer.
- Used in cable television (CATV) and broadband internet connections.
- Offers better shielding against interference compared to twisted pair cables.
- Data Transmission:
- Supports higher data rates than twisted pair cables.
- Suitable for transmitting television signals and high-speed data.
3. Fiber Optic Cable:
- Characteristics:
- Uses thin strands of glass or plastic to transmit data as pulses of light.
- Offers high bandwidth, immunity to electromagnetic interference, and long-distance transmission.
- Resistant to environmental factors such as moisture and temperature.
- Data Transmission:
- Suitable for high-speed and long-distance communication.
- Widely used in telecommunications networks, internet backbones, and data centers.
4. Radio Waves:
- Characteristics:
- Used for wireless communication, including radio and television broadcasting.
- Part of the electromagnetic spectrum.
- Data Transmission:
- Supports broadcast communication over a wide area.
- Common in radio and television broadcasting.
5. Microwaves:
- Characteristics:
- High-frequency electromagnetic waves.
- Used in point-to-point communication, such as long-distance telephone and television transmission.
- Data Transmission:
- Suitable for long-distance communication, including point-to-point links between microwave towers.
- Used for backbone links in communication networks.
6. Infrared Waves:
- Characteristics:
- Uses infrared light for communication.
- Common in devices like remote controls and short-range wireless data transfer.
- Data Transmission:
- Suitable for short-range communication within a confined space.
- Common in consumer electronics for device control.
7. Satellite Communication:
- Characteristics:
- Involves communication via signals transmitted to and received from satellites.
- Uses radio waves or microwaves for communication.
- Data Transmission:
- Suitable for long-distance communication, including television broadcasting and global positioning systems (GPS).
- Provides coverage over large geographic areas.
8. Bluetooth:
- Characteristics:
- Short-range wireless technology.
- Operates in the unlicensed Industrial, Scientific, and Medical (ISM) band.
- Data Transmission:
- Designed for short-range communication between devices (typically within 10 meters).
- Used in applications like wireless headphones, keyboards, and file transfer between devices.
9. Wi-Fi:
- Characteristics:
- Wireless technology for LAN communication.
- Operates in the 2.4 GHz and 5 GHz frequency bands.
- Data Transmission:
- Supports medium to high-speed data rates.
- Widely used for wireless internet access in homes, offices, and public spaces.
Data Transmission and Data Networking:
Data Transmission:
Data transmission is the process of sending digital or analog data signals from one location to another. It involves the movement of information between devices, and this transmission can occur through various types of communication media. The primary goal is to ensure that data is accurately and efficiently delivered to the intended destination. Key aspects of data transmission include:
- Modes of Data Transmission:
- Simplex:
- Definition: In simplex communication, data transmission occurs in only one direction, similar to a one-way street. One device is the sender, and the other device is the receiver.
- Characteristics:
- Unidirectional: Communication flows in a single direction.
- One-way communication: Data travels from the sender to the receiver, and the receiver cannot send data back.
- Examples: Television broadcasting, public address systems.
- Half-Duplex:
- Definition: In half-duplex communication, data transmission can occur in both directions, but not simultaneously. Devices can both send and receive, but not at the same time.
- Characteristics:
- Bidirectional: Communication can occur in both directions.
- One-way at a time: Devices take turns sending and receiving data.
- Examples: Walkie-talkies, traditional two-way radios.
- Full-Duplex:
- Definition: In full-duplex communication, data transmission can occur in both directions simultaneously, allowing for two-way communication.
- Characteristics:
- Bidirectional: Communication occurs in both directions concurrently.
- Simultaneous transmission: Devices can send and receive data simultaneously without waiting for turns.
- Examples: Telephone conversations, video conferencing, most modern communication systems.
- Simplex:

- Transmission Types:Serial Transmission:
- Definition: In serial transmission, data is sent one bit at a time over a single channel. The bits are transmitted sequentially, one after the other, over the same communication path.
- Characteristics:
- Single Channel: Uses a single communication path or wire for transmitting data.
- Sequential Transmission: Bits are sent in a consecutive order.
- Simple Implementation: Easier to implement than parallel transmission.
- Applications:
- Commonly used in long-distance communication and scenarios where a single channel is sufficient.
- Examples include serial communication ports (e.g., RS-232) and serial data transmission in networking.
Parallel Transmission:
- Definition: In parallel transmission, multiple bits are sent simultaneously over multiple channels or wires. Each bit has its own dedicated channel, and all bits are transmitted concurrently.
- Characteristics:
- Multiple Channels: Uses multiple communication paths or wires for simultaneous transmission of bits.
- Simultaneous Transmission: Multiple bits are transmitted at the same time.
- Higher Bandwidth: Can achieve higher data transfer rates compared to serial transmission.
- Applications:
- Commonly used for short-distance communication within computer systems (e.g., parallel buses inside computers).
- Examples include parallel ports, parallel ATA (PATA) for connecting hard drives, and parallel communication in certain network interfaces.
Comparison:
- Serial Transmission:
- Pros: Simplified hardware design, suitable for long-distance communication.
- Cons: Slower data transfer rates compared to parallel transmission for short distances.
- Parallel Transmission:
- Pros: Faster data transfer rates for short distances, simultaneous transmission of multiple bits.
- Cons: Requires more complex hardware design, may be susceptible to signal skew and interference.
- Data Transmission Rate:The data transmission rate, also known as the data transfer rate or bitrate, refers to the speed at which data is transmitted between devices over a communication channel. It is measured in bits per second (bps), and larger units such as kilobits per second (Kbps), megabits per second (Mbps), or gigabits per second (Gbps) are commonly used to express higher speeds. Here are key points related to data transmission rate:
- Units of Measurement:
- Bits per Second (bps): The basic unit representing the number of bits transmitted in one second.
- Kilobits per Second (Kbps): Equivalent to 1,000 bps.
- Megabits per Second (Mbps): Equivalent to 1,000 Kbps or 1,000,000 bps.
- Gigabits per Second (Gbps): Equivalent to 1,000 Mbps or 1,000,000 Kbps or 1,000,000,000 bps.
- Communication Medium and Technology Impact:
- The data transmission rate depends on the characteristics of the communication medium and the technology used for transmission.
- Different transmission media (e.g., copper cables, fiber optics, wireless) and technologies (e.g., modulation techniques) have varying capacities for data transfer.
- Factors Influencing Transmission Rate:
- Bandwidth: The available frequency range for data transmission influences the potential data transmission rate. Higher bandwidth allows for higher transmission rates.
- Signal-to-Noise Ratio (SNR): A higher SNR supports reliable communication and higher data rates.
- Modulation Techniques: The method of encoding data onto the carrier signal affects the efficiency of data transmission.
- Transmission Medium: Different mediums (copper, fiber, wireless) have different inherent properties that impact data transmission rates.
- Real vs. Effective Data Rates:
- The actual data transfer rate, known as the effective data rate, may be less than the theoretical maximum due to factors such as protocol overhead, error correction, and network congestion.
- Applications:
- The required data transmission rate varies based on the application. For example, multimedia streaming, online gaming, and real-time communication applications demand higher data rates.
- Measuring Throughput:
- Throughput refers to the actual data transfer rate achieved in a real-world scenario. It considers factors such as protocol efficiency and network conditions.
- Speeds in Modern Networks:
- In modern networks, especially for broadband internet and high-speed networks, data transmission rates are often expressed in Mbps or Gbps.
- Units of Measurement:
- Data Transmission Modes:
- Simplex:
- Definition: In simplex communication, data transmission occurs in only one direction, similar to a one-way street. One device is the sender, and the other device is the receiver.
- Characteristics:
- Unidirectional: Communication flows in a single direction.
- One-way communication: Data travels from the sender to the receiver, and the receiver cannot send data back.
- Examples: Television broadcasting, public address systems.
- Half-Duplex:
- Definition: In half-duplex communication, data transmission can occur in both directions, but not simultaneously. Devices can both send and receive, but not at the same time.
- Characteristics:
- Bidirectional: Communication can occur in both directions.
- One-way at a time: Devices take turns sending and receiving data.
- Examples: Walkie-talkies, traditional two-way radios.
- Full-Duplex:
- Definition: In full-duplex communication, data transmission can occur in both directions simultaneously, allowing for two-way communication.
- Characteristics:
- Bidirectional: Communication occurs in both directions concurrently.
- Simultaneous transmission: Devices can send and receive data simultaneously without waiting for turns.
- Examples: Telephone conversations, video conferencing, most modern communication systems.
- Simplex:
- Error Detection and Correction:In data communication, errors can occur during the transmission of information due to various factors such as noise, interference, or signal degradation. Error is a condition when the receiver’s information does not match the sender’s information. During transmission, digital signals suffer from noise that can introduce errors in the binary bits traveling from sender to receiver. That means a 0 bit may change to 1 or a 1 bit may change to 0. Error detection and correction techniques are employed to identify and rectify these errors, ensuring the integrity of the transmitted data.Types of ErrorsSingle-Bit Error:A single-bit error refers to a type of data transmission error that occurs when one bit (i.e., a single binary digit) of a transmitted data unit is altered during transmission, resulting in an incorrect or corrupted data unit.

Multiple-Bit Error
A multiple-bit error is an error type that arises when more than one bit in a data transmission is affected. Although multiple-bit errors are relatively rare when compared to single-bit errors, they can still occur, particularly in high-noise or high-interference digital environments.

Burst Error
When several consecutive bits are flipped mistakenly in digital transmission, it creates a burst error. This error causes a sequence of consecutive incorrect values.
To detect errors, a common technique is to introduce redundancy bits that provide additional information. Various techniques for error detection include::
- Simple Parity Check
- Two-dimensional Parity Check
- Checksum
- Cyclic Redundancy Check (CRC)
Error Detection Methods
Simple Parity Check
Simple-bit parity is a simple error detection method that involves adding an extra bit to a data transmission. It works as:
- 1 is added to the block if it contains an odd number of 1’s, and
- 0 is added if it contains an even number of 1’s
This scheme makes the total number of 1’s even, that is why it is called even parity checking.
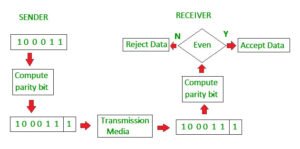
Disadvantages
- Single Parity check is not able to detect even no. of bit error.
- For example, the Data to be transmitted is 101010. Codeword transmitted to the receiver is 1010101
Two-dimensional Parity Check
Two-dimensional Parity check bits are calculated for each row, which is equivalent to a simple parity check bit. Parity check bits are also calculated for all columns, then both are sent along with the data. At the receiving end, these are compared with the parity bits calculated on the received data.

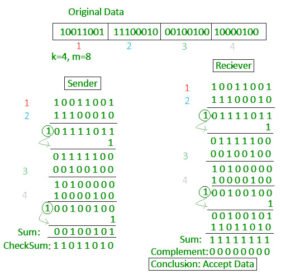
Checksum
Checksum error detection is a method used to identify errors in transmitted data. The process involves dividing the data into equally sized segments and using a 1’s complement to calculate the sum of these segments. The calculated sum is then sent along with the data to the receiver. At the receiver’s end, the same process is repeated and if all zeroes are obtained in the sum, it means that the data is correct.
Checksum – Operation at Sender’s Side
- Firstly, the data is divided into k segments each of m bits.
- On the sender’s end, the segments are added using 1’s complement arithmetic to get the sum. The sum is complemented to get the checksum.
- The checksum segment is sent along with the data segments.
Checksum – Operation at Receiver’s Side
- At the receiver’s end, all received segments are added using 1’s complement arithmetic to get the sum. The sum is complemented.
- If the result is zero, the received data is accepted; otherwise discarded.
Disadvantages
- If one or more bits of a segment are damaged and the corresponding bit or bits of opposite value in a second segment are also damaged.
Data Networking:
Data networking involves the interconnection of multiple computing devices to enable communication, resource sharing, and collaboration. Networks can vary in size and scope, ranging from small local area networks (LANs) within a single building to large-scale global networks. Key aspects of data networking include:
- Network Components: The main components required for software installation are those found in a computer network. A few crucial parts of a network include the hub, router, modem, switch, cable, and NIC. Certain components of the network can also be eliminated, depending on the kind of network we need to install.
- Following are the major components required to install a network:
NIC:
- NIC stands for network interface card.
- NIC is a hardware component used to connect a computer with another computer onto a network
- It can support a transfer rate of 10,100 to 1000 Mb/s.
- The MAC address or physical address is encoded on the network card chip which is assigned by the IEEE to identify a network card uniquely. The MAC address is stored in the PROM (Programmable read-only memory).
- Following are the major components required to install a network:
There are two types of NIC:
Wired NIC: The Wired NIC is present inside the motherboard. Cables and connectors are used with wired NIC to transfer data.
Wireless NIC: The wireless NIC contains the antenna to obtain the connection over the wireless network. For example, laptop computer contains the wireless NIC.
Hub:
A hub is a piece of hardware that splits a network connection amongst several devices. A computer sends a cable to the Hub initially when it wants to obtain information from a network. Hub will send out a network-wide broadcast of this request. Every device will verify whether or not the request is theirs. The request will be rejected otherwise.
The Hub’s operation uses more bandwidth and restricts the volume of communication. Hubs are no longer in use; instead, more sophisticated computer network components like switches and routers are used in its place.
Switch : A physical component that joins several computer network devices is called a switch. Compared to a Hub, a Switch has more sophisticated functions. The Switch is equipped with an updated table that determines whether or not data is transferred. Switch uses the physical address in the incoming message to determine which destination is best for the message. Unlike the Hub, a switch does not broadcast the message to the whole network. It chooses which device the message should be sent to. As a result, a direct link between the source and the destination is provided by the switch. It makes the network run faster.
Router
- A router is a hardware device which is used to connect a LAN with an internet connection. It is used to receive, analyze and forward the incoming packets to another network.
- A router works in a Layer 3 (Network layer) of the OSI Reference model.
- A router forwards the packet based on the information available in the routing table.
- It determines the best path from the available paths for the transmission of the packet.
Advantages Of Router:
- Security: The information which is transmitted to the network will traverse the entire cable, but the only specified device which has been addressed can read the data.
- Reliability: If the server has stopped functioning, the network goes down, but no other networks are affected that are served by the router.
- Performance: Router enhances the overall performance of the network. Suppose there are 24 workstations in a network generates a same amount of traffic. This increases the traffic load on the network. Router splits the single network into two networks of 12 workstations each, reduces the traffic load by half.
Modem
- A modem is a hardware device that allows the computer to connect to the internet over the existing telephone line.
- A modem is not integrated with the motherboard rather than it is installed on the PCI slot found on the motherboard.
- It stands for Modulator/Demodulator. It converts the digital data into an analog signal over the telephone lines.
Based on the differences in speed and transmission rate, a modem can be classified in the following categories:
- Standard PC modem or Dial-up modem
- Cellular Modem
- Cable modem
Types of Networks:
-
-
PAN: (Personal Area Network) is a computer network formed around a person. It generally consists of a computer, mobile, or personal digital assistant. PAN can be used for establishing communication among these personal devices for connecting to a digital network and the internet.
Characteristics of PAN
Below are the main characteristics of PAN:
- It is mostly personal devices network equipped within a limited area.
- Allows you to handle the interconnection of IT devices at the surrounding of a single user.
- PAN includes mobile devices, tablet, and laptop.
- It can be wirelessly connected to the internet called WPAN.
- Appliances use for PAN: cordless mice, keyboards, and Bluetooth systems.
Advantages of PAN
Here are the important pros/benefits of PAN network:
- PAN networks are relatively secure and safe
- It offers only short-range solution up to ten meters
- Strictly restricted to a small area
Disadvantages of PAN
Here are the cons/drawbacks of using PAN network:
- It may establish a bad connection to other networks at the same radio bands.
- Distance limits.
-
Local Area Network: A Local Area Network (LAN) is a group of computer and peripheral devices which are connected in a limited area such as school, laboratory, home, and office building. It is a widely useful network for sharing resources like files, printers, games, and other application. The simplest type of LAN network is to connect computers and a printer in someone’s home or office. In general, LAN will be used as one type of transmission medium. It is a network which consists of less than 5000 interconnected devices across several buildings.
Characteristics of LAN
Here are the important characteristics of a LAN network:
- It is a private network, so an outside regulatory body never controls it.
- LAN operates at a relatively higher speed compared to other WAN systems.
- There are various kinds of media access control methods like token ring and ethernet
Advantages of LAN
Here are the pros/benefits of LAN:
- Computer resources like hard-disks, DVD-ROM, and printers can share local area networks. This significantly reduces the cost of hardware purchases.
- You can use the same software over the network instead of purchasing the licensed software for each client in the network.
- Data of all network users can be stored on a single hard disk of the server computer.
- You can easily transfer data and messages over networked computers.
- It will be easy to manage data at only one place, which makes data more secure.
- Local Area Network offers the facility to share a single internet connection among all the LAN users.
Disadvantages of LAN
Here are the cons/drawbacks of LAN:
- LAN will indeed save cost because of shared computer resources, but the initial cost of installing Local Area Networks is quite high.
- The LAN admin can check personal data files of every LAN user, so it does not offer good privacy.
- Unauthorized users can access critical data of an organization in case LAN admin is not able to secure centralized data repository.
- Local Area Network requires a constant LAN administration as there are issues related to software setup and hardware failures.
Metropolitan Area Network : A Metropolitan Area Network or MAN is consisting of a computer network across an entire city, college campus, or a small region. This type of network is large than a LAN, which is mostly limited to a single building or site. Depending upon the type of configuration, this type of network allows you to cover an area from several miles to tens of miles.
Characteristics of MAN
Here are important characteristics of the MAN network:
- It mostly covers towns and cities in a maximum 50 km range
- Mostly used medium is optical fibers, cables
- Data rates adequate for distributed computing applications.
Advantages of MAN
Here are the pros/benefits of MAN network:
- It offers fast communication using high-speed carriers, like fiber optic cables.
- It provides excellent support for an extensive size network and greater access to WANs.
- The dual bus in MAN network provides support to transmit data in both directions concurrently.
- A MAN network mostly includes some areas of a city or an entire city.
Disadvantages of MAN
Here are drawbacks/cons of using the MAN network:
- You need more cable to establish MAN connection from one place to another.
- In MAN network it is tough to make the system secure from hackers
WAN: (Wide Area Network) is another important computer network that which is spread across a large geographical area. WAN network system could be a connection of a LAN which connects with other LAN’s using telephone lines and radio waves. It is mostly limited to an enterprise or an organization.
Characteristics of WAN
Below are the characteristics of WAN:
- The software files will be shared among all the users; therefore, all can access to the latest files.
- Any organization can form its global integrated network using WAN.
Advantages of WAN
Here are the benefits/pros of WAN:
- WAN helps you to cover a larger geographical area. Therefore business offices situated at longer distances can easily communicate.
- Contains devices like mobile phones, laptop, tablet, computers, gaming consoles, etc.
- WLAN connections work using radio transmitters and receivers built into client devices.
Disadvantages of WAN
Here are the drawbacks/cons of WAN network:
- The initial setup cost of investment is very high.
- It is difficult to maintain the WAN network. You need skilled technicians and network administrators.
- There are more errors and issues because of the wide coverage and the use of different technologies.
- It requires more time to resolve issues because of the involvement of multiple wired and wireless technologies.
- Offers lower security compared to other types of network in computer.
Home Area Network (HAN)
A Home Area Network is always built using two or more interconnected computers to form a local area network (LAN) within the home. For example, in the United States, about 15 million homes have more than one computer.
These types of network connections help computer owners to interconnect with multiple computers. This network allows sharing files, programs, printers, and other peripherals.
Enterprise Private Network
Enterprise private network (EPN) networks are build and owned by businesses that want to securely connect numerous locations in order to share various computer resources.
Network Topologies:
Network topologies define the physical or logical layout of nodes and the connections between them in a network. Here are brief descriptions of the mentioned network topologies:
-
- Star Topology:
- Description: In a star topology, all nodes are connected to a central hub or switch. The central hub acts as a mediator for data transmission between connected devices.
- Characteristics:
- Centralized structure with a focal point (hub or switch).
- Easy to install and manage.
- Fault isolation: Issues in one connection typically don’t affect others.
- Relies heavily on the central hub; failure of the hub can disrupt the entire network.
- Example: Ethernet LANs using a central switch.
- Bus Topology:
- Description: In a bus topology, nodes are connected along a single communication line, often referred to as a bus. Each node receives the transmitted data but only processes information addressed to it.
- Characteristics:
- Single communication line shared by all nodes.
- Simple and cost-effective.
- Easy to extend by adding new nodes.
- Susceptible to collisions and signal degradation, especially as the number of nodes increases.
- Example: Older Ethernet LANs using coaxial cables.
- Ring Topology:
- Description: In a ring topology, each node is connected to exactly two other nodes, forming a closed loop or ring. Data circulates in one direction around the ring.
- Characteristics:
- Circular structure with data moving in a specific direction.
- Uniform data transfer, each node has exactly two neighbors.
- Reliability can be impacted if one node or connection fails, breaking the ring.
- Less susceptible to collisions compared to bus topology.
- Example: Token Ring networks (less common today).
- Mesh Topology:
- Description: In a mesh topology, nodes are interconnected, providing multiple paths for data transmission between any two nodes. This creates a redundant and fault-tolerant network.
- Characteristics:
- Redundant paths enhance reliability and fault tolerance.
- High implementation cost due to numerous connections.
- Complex to design and manage.
- Excellent performance and reliability if well-implemented.
- Example: Internet backbone networks and critical infrastructure systems.
- Star Topology:
- Communication Protocols:Communication protocols are sets of rules and conventions that govern the exchange of data between devices in a network. They define how data is formatted, transmitted, received, and interpreted, ensuring a standardized and efficient communication process. Here are key points about communication protocols:
- Definition:
- Communication protocols provide a common language that devices on a network can understand and use to communicate.
- They specify the format and structure of data, the sequence of operations, error handling, and other aspects of the communication process.
- Role of Protocols:
- Data Formatting: Protocols define how data is structured, including headers, footers, and any additional information required for transmission.
- Addressing: Protocols specify how devices are addressed on the network, allowing data to be directed to the intended recipient.
- Error Detection and Correction: Many protocols include mechanisms for detecting and, in some cases, correcting errors that may occur during transmission.
- Flow Control: Protocols manage the pace of data exchange to ensure that sending and receiving devices operate at compatible speeds.
- Security: Some protocols incorporate security features such as encryption and authentication to protect data during transmission.
- Examples of Communication Protocols:
- TCP/IP (Transmission Control Protocol/Internet Protocol):
- TCP/IP Model helps you to determine how a specific computer should be connected to the internet and how data should be transmitted between them. It helps you to create a virtual network when multiple computer networks are connected together. The purpose of TCP/IP model is to allow communication over large distances.
- TCP/IP (Transmission Control Protocol/Internet Protocol):
- Definition:
TCP Characteristics
Here, are the essential characteristics of TCP IP protocol:
- Support for a flexible TCP/IP architecture
- Adding more system to a network is easy.
- In TCP IP protocols suite, the network remains intact until the source, and destination machines were functioning properly.
- TCP is a connection-oriented protocol.
- TCP offers reliability and ensures that data which arrives out of sequence should put back into order.
- TCP allows you to implement flow control, so sender never overpowers a receiver with data.
Four Layers of TCP/IP model
In this TCP/IP tutorial, we will explain different layers and their functionalities in TCP/IP model:
TCP/IP is a layered server architecture system in which each layer is defined according to a specific function to perform. All these four TCP IP layers work collaboratively to transmit the data from one layer to another.
- Application Layer
- Transport Layer
- Internet Layer
- Network Interface
Application Layer
Application layer interacts with an application program, which is the highest level of OSI model. The application layer is the OSI layer, which is closest to the end-user. It means the OSI application layer allows users to interact with other software application.
Application layer interacts with software applications to implement a communicating component. The interpretation of data by the application program is always outside the scope of the OSI model.
Example of the application layer is an application such as file transfer, email, remote login, etc.
The function of the Application Layers are
- Application-layer helps you to identify communication partners, determining resource availability, and synchronizing communication.
- It allows users to log on to a remote host
- This layer provides various e-mail services
- This application offers distributed database sources and access for global information about various objects and services.
Transport Layer
Transport layer builds on the network layer in order to provide data transport from a process on a source system machine to a process on a destination system. It is hosted using single or multiple networks, and also maintains the quality of service functions.
It determines how much data should be sent where and at what rate. This layer builds on the message which are received from the application layer. It helps ensure that data units are delivered error-free and in sequence.
Transport layer helps you to control the reliability of a link through flow control, error control, and segmentation or de-segmentation.
The transport layer also offers an acknowledgment of the successful data transmission and sends the next data in case no errors occurred. TCP is the best-known example of the transport layer.
Important functions of Transport Layers
- It divides the message received from the session layer into segments and numbers them to make a sequence.
- Transport layer makes sure that the message is delivered to the correct process on the destination machine.
- It also makes sure that the entire message arrives without any error else it should be retransmitted.
Internet Layer
An internet layer is a second layer of TCP/IP layes of the TCP/IP model. It is also known as a network layer. The main work of this layer is to send the packets from any network, and any computer still they reach the destination irrespective of the route they take.
The Internet layer offers the functional and procedural method for transferring variable length data sequences from one node to another with the help of various networks.
Message delivery at the network layer does not give any guaranteed to be reliable network layer protocol.
Layer-management protocols that belong to the network layer are:
- Routing protocols
- Multicast group management
- Network-layer address assignment.
The Network Interface Layer
Network Interface Layer is this layer of the four-layer TCP/IP model. This layer is also called a network access layer. It helps you to defines details of how data should be sent using the network.
It also includes how bits should optically be signaled by hardware devices which directly interfaces with a network medium, like coaxial, optical, coaxial, fiber, or twisted-pair cables.
A network layer is a combination of the data line and defined in the article of OSI reference model. This layer defines how the data should be sent physically through the network. This layer is responsible for the transmission of the data between two devices on the same network.
-
-
-
-
- Ethernet:Ethernet is a widely adopted Local Area Network (LAN) technology that plays a crucial role in connecting devices within a limited geographical area, such as an office, campus, or home. It defines both the physical and data link layers of the OSI model and employs a specific set of protocols for various functions.
- Here are key points about Ethernet:
- LAN Technology:
- Ethernet is primarily designed for use in Local Area Networks (LANs), providing a cost-effective and efficient means of connecting devices in proximity to each other.
- OSI Model Layers:
- Ethernet operates at both the Physical Layer (Layer 1) and the Data Link Layer (Layer 2) of the OSI model.
- The Physical Layer involves the transmission of raw binary data over the physical medium, such as cables or fiber optics.
- The Data Link Layer manages communication between directly connected nodes, including error detection, framing, and MAC addressing.
- Frame Formatting:
- Ethernet uses a specific frame format to organize and structure data for transmission.
- A typical Ethernet frame includes fields for source and destination MAC addresses, type/length, data payload, and a Frame Check Sequence (FCS) for error detection.
- Collision Detection:
- Ethernet employs a carrier-sense multiple access with collision detection (CSMA/CD) protocol to manage access to the shared communication medium.
- Before transmitting data, a device listens to the network to detect if the medium is busy. If it is clear, the device proceeds with transmission. If a collision occurs (two devices transmitting simultaneously), both devices back off and retry after a random time interval.
- Media Access Control (MAC) Addressing:
- Each network interface card (NIC) on an Ethernet network is assigned a unique Media Access Control (MAC) address.
- The MAC address is a hardware address that identifies the specific network interface and is used for addressing and communication within the data link layer.
Advantages:
- Cost-Effective: Ethernet is a cost-effective solution for connecting devices within a local area.
- Ubiquity: Ethernet is widely adopted and supported, making it a standard for LAN connectivity.
- Scalability: Ethernet can be easily scaled to accommodate the growth of a network.
- LAN Technology:
-
-
- HTTP/HTTPS (Hypertext Transfer Protocol/Secure):HTTP (Hypertext Transfer Protocol):
- Usage:
- HTTP is a protocol used for transmitting hypertext (text with links) over the internet.
- It is the foundation of data communication on the World Wide Web.
- Functionality:
- HTTP facilitates the transfer of various types of media, including text, images, videos, and other multimedia content.
- It operates on a client-server model, where a client (such as a web browser) sends requests, and a server responds with the requested resources.
- Stateless Protocol:
- HTTP is a stateless protocol, meaning each request from a client to a server is independent and not dependent on previous requests.
- The server does not retain information about the client’s previous requests.
- URL Structure:
- Uniform Resource Locators (URLs) are used to identify resources on the web. HTTP URLs typically start with “http://” (e.g., http://www.example.com).
HTTPS (Hypertext Transfer Protocol Secure):
- Encryption:
- HTTPS is the secure version of HTTP that adds a layer of encryption to the communication.
- It uses SSL (Secure Sockets Layer) or its successor, TLS (Transport Layer Security), to secure data transmitted between the client and the server.
- Security Features:
- Encrypts data to prevent unauthorized access during transmission.
- Authenticates the identity of the website to ensure users are connecting to the intended server and not an imposter.
- URL Structure:
- URLs for HTTPS use “https://” (e.g., https://www.example.com).
- The use of HTTPS is indicated by a padlock icon in the browser’s address bar, providing users with visual assurance of a secure connection.
- Use Cases:
- HTTPS is crucial for securing sensitive information, such as login credentials, financial transactions, and personal data exchanged on websites.
- Data Integrity:
- HTTPS ensures the integrity of data during transmission, preventing tampering or modification of the content by malicious entities.
- SEO Impact:
- Search engines may prioritize websites using HTTPS, as it provides a more secure and trustworthy user experience.
- SSL/TLS Certificates:
- Websites using HTTPS need SSL/TLS certificates, which are issued by Certificate Authorities (CAs) to verify the authenticity of the website.
- Usage:
- SMTP (Simple Mail Transfer Protocol):
- SMTP stands for Simple Mail Transfer Protocol.
- SMTP is a set of communication guidelines that allow software to transmit an electronic mail over the internet is called Simple Mail Transfer Protocol.
- It is a program used for sending messages to other computer users based on e-mail addresses.
- It provides a mail exchange between users on the same or different computers, and it also supports:
- It can send a single message to one or more recipients.
- Sending message can include text, voice, video or graphics.
- It can also send the messages on networks outside the internet.
- The main purpose of SMTP is used to set up communication rules between servers. The servers have a way of identifying themselves and announcing what kind of communication they are trying to perform. They also have a way of handling the errors such as incorrect email address. For example, if the recipient address is wrong, then receiving server reply with an error message of some kind.
-
Working of SMTP
- Composition of Mail: A user sends an e-mail by composing an electronic mail message using a Mail User Agent (MUA). Mail User Agent is a program which is used to send and receive mail. The message contains two parts: body and header. The body is the main part of the message while the header includes information such as the sender and recipient address. The header also includes descriptive information such as the subject of the message. In this case, the message body is like a letter and header is like an envelope that contains the recipient’s address.
- Submission of Mail: After composing an email, the mail client then submits the completed e-mail to the SMTP server by using SMTP on TCP port 25.
- Delivery of Mail: E-mail addresses contain two parts: username of the recipient and domain name. For example, vivek@gmail.com, where “vivek” is the username of the recipient and “gmail.com” is the domain name.
If the domain name of the recipient’s email address is different from the sender’s domain name, then MSA will send the mail to the Mail Transfer Agent (MTA). To relay the email, the MTA will find the target domain. It checks the MX record from Domain Name System to obtain the target domain. The MX record contains the domain name and IP address of the recipient’s domain. Once the record is located, MTA connects to the exchange server to relay the message. - Receipt and Processing of Mail: Once the incoming message is received, the exchange server delivers it to the incoming server (Mail Delivery Agent) which stores the e-mail where it waits for the user to retrieve it.
- Access and Retrieval of Mail: The stored email in MDA can be retrieved by using MUA (Mail User Agent). MUA can be accessed by using login and password.
FTP (File Transfer Protocol):
- FTP is a standard internet protocol provided by TCP/IP used for transmitting the files from one host to another.
- It is mainly used for transferring the web page files from their creator to the computer that acts as a server for other computers on the internet.
- It is also used for downloading the files to computer from other servers.
Objectives of FTP
- It provides the sharing of files.
- It is used to encourage the use of remote computers.
- It transfers the data more reliably and efficiently.
Advantages of FTP:
- Speed: One of the biggest advantages of FTP is speed. The FTP is one of the fastest way to transfer the files from one computer to another computer.
- Efficient: It is more efficient as we do not need to complete all the operations to get the entire file.
- Security: To access the FTP server, we need to login with the username and password. Therefore, we can say that FTP is more secure.
- Back & forth movement: FTP allows us to transfer the files back and forth. Suppose you are a manager of the company, you send some information to all the employees, and they all send information back on the same server.
Disadvantages of FTP:
- The standard requirement of the industry is that all the FTP transmissions should be encrypted. However, not all the FTP providers are equal and not all the providers offer encryption. So, we will have to look out for the FTP providers that provides encryption.
- FTP serves two operations, i.e., to send and receive large files on a network. However, the size limit of the file is 2GB that can be sent. It also doesn’t allow you to run simultaneous transfers to multiple receivers.
- Passwords and file contents are sent in clear text that allows unwanted eavesdropping. So, it is quite possible that attackers can carry out the brute force attack by trying to guess the FTP password.
- Networking Standards:
- Networking standards define the rules for data communications that are needed for interoperability of networking technologies and processes. Standards help in creating and maintaining open markets and allow different vendors to compete on the basis of the quality of their products while being compatible with existing market products.
Types of Standards
Standards are of two types
- De facto − These are the standards that are followed without any formal plan or approval by any organization. They have come into existence due to traditions or facts. For example, the HTTP had started as a de facto standard.
- De jure − These standards are the ones which have been adopted through legislation by any officially recognized standards organization. Most of the communication standards that are used today are de jure standards.
- Network Security:
- Network security is a critical aspect of information technology that focuses on implementing measures to safeguard the confidentiality, integrity, and availability of data transmitted over a network. The primary goals of network security are to prevent unauthorized access, protect against data tampering or theft, and ensure the continuous and reliable operation of network services. Here are some key components and measures commonly associated with network security:
- Firewalls: Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the internet. They monitor and control incoming and outgoing network traffic based on predetermined security rules, helping to prevent unauthorized access and potential cyber threats.
- Encryption: Encryption is the process of converting data into a coded format that can only be deciphered by authorized parties with the appropriate decryption key. It ensures the confidentiality of sensitive information during transmission or storage.
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): IDS and IPS are security mechanisms designed to detect and respond to unauthorized or malicious activities on a network. IDS monitors network traffic for suspicious patterns, while IPS takes proactive measures to prevent or block potentially harmful traffic.
- Virtual Private Network (VPN): VPNs establish secure, encrypted communication channels over public networks, such as the internet. They are commonly used to provide secure remote access to a corporate network, ensuring the confidentiality of data transmitted between remote users and the organization’s internal resources.
- Access Control: Access control mechanisms restrict and manage user access to network resources. This includes user authentication, authorization, and accounting (AAA) systems that ensure only authorized individuals have access to specific data or network segments.
- Network Segmentation: Dividing a network into segments or zones helps contain potential security breaches. By separating different parts of the network, even if one segment is compromised, it minimizes the impact on the overall network.
- Patch Management: Regularly updating software, operating systems, and network devices with the latest security patches is crucial to address vulnerabilities and protect against known exploits.
- Network security is a critical aspect of information technology that focuses on implementing measures to safeguard the confidentiality, integrity, and availability of data transmitted over a network. The primary goals of network security are to prevent unauthorized access, protect against data tampering or theft, and ensure the continuous and reliable operation of network services. Here are some key components and measures commonly associated with network security:
- Wireless Networking:
- Wireless networking is a technology that enables communication between devices without the need for physical cables. This type of networking has become ubiquitous in various settings, providing flexibility, mobility, and convenience for users. Some key aspects and technologies associated with wireless networking include:
- Wi-Fi (Wireless Fidelity): Wi-Fi is a widely used wireless networking technology that allows devices to connect to a local area network (LAN) without the need for physical cables. It is commonly used for internet access in homes, businesses, public spaces, and educational institutions. Wi-Fi operates on radio frequencies and is defined by various standards, such as IEEE 802.11a/b/g/n/ac/ax.
- Bluetooth: Bluetooth is a short-range wireless communication technology that facilitates data exchange between devices, such as smartphones, laptops, headphones, and peripherals. It is commonly used for tasks like file transfer, audio streaming, and connecting input devices like keyboards and mice to computers. Bluetooth operates on the 2.4 GHz frequency range.
- Cellular Networks: Cellular networks provide wireless communication for mobile devices using a system of interconnected base stations. They enable voice calls, text messaging, and data transfer over long distances. Common cellular technologies include 3G (Third Generation), 4G LTE (Fourth Generation Long-Term Evolution), and 5G (Fifth Generation), each offering improvements in data speed, latency, and capacity.
- Wireless LAN (WLAN): Wireless LANs use radio waves to establish connections between devices within a limited geographic area, such as a home, office, or campus. Wi-Fi is a common implementation of wireless LAN technology. WLANs provide mobility and flexibility, allowing users to connect to the network from different locations within the coverage area.
- Mesh Networking: Mesh networking is a decentralized approach to wireless communication where each device in the network acts as a node, relaying data for other devices. This can enhance coverage and reliability, particularly in large or challenging environments.
- Near Field Communication (NFC): NFC is a short-range wireless communication technology that allows devices to exchange data when placed in close proximity. It is often used for contactless payments, pairing devices, and sharing information between smartphones.
- Zigbee and Z-Wave: These are wireless communication standards designed for low-power, short-range applications in smart homes and Internet of Things (IoT) devices. They are commonly used for home automation and smart device connectivity.
- Satellite Communication: While not as common for everyday use, satellite communication provides wireless connectivity over long distances, making it suitable for remote areas or situations where traditional network infrastructure is unavailable.
- Wireless networking is a technology that enables communication between devices without the need for physical cables. This type of networking has become ubiquitous in various settings, providing flexibility, mobility, and convenience for users. Some key aspects and technologies associated with wireless networking include: